We will start by introducing you to the basic concepts and terminologies used in red team, cyber security and warfare, providing you with a foundation for understanding the more advanced topics that we will cover later in the course. Next, we will delve into the world of cyber operations and show you how these operations are organized and executed. We will discuss how powerful nations are developing cyber capabilities and how this is changing the landscape of warfare. As we move deeper, we will cover a range of advanced topics, including myths of anonymity, recent ransomware attacks, advanced persistent threats which includes advanced malwares. You will also learn about the operational mistakes that nation state hackers have made while conducting sophisticated attacks, and how organizations can defend against these attacks.
| Course Price | Original price was: $100.00.$8.00Current price is: $8.00. |
Course Description
What you’ll learn
- 145+ videos (30+ hours) to teach you Advanced Penetration Testing from scratch.
- Use 50+ hacking tools
- 85+ hands-on real-life hacking examples.
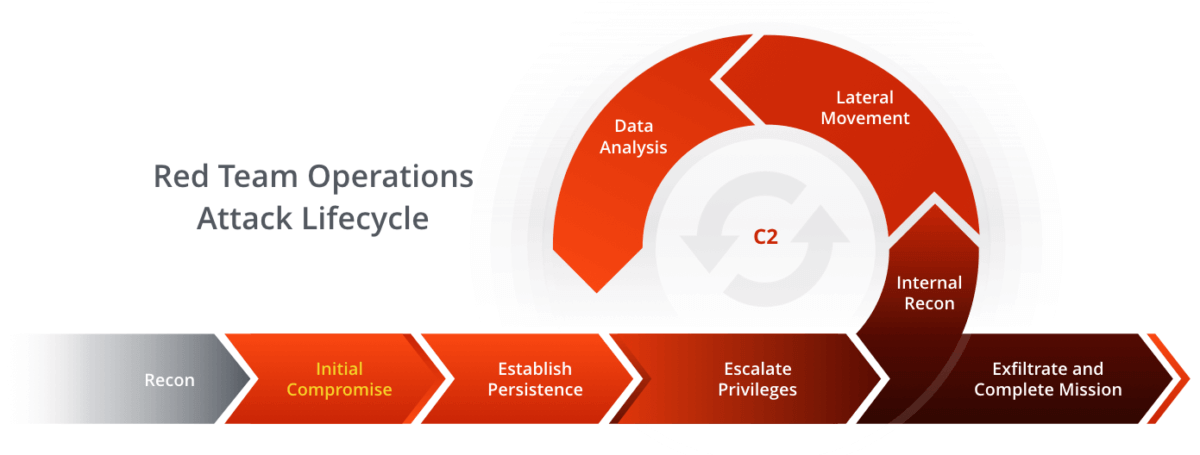
- Use threat intelligence to study adversaries for emulation
- Build an adversary emulation plan
- Map actions to MITRE® ATT&CK™ to aid in communicating with the Blue Team
- Establish resilient, advanced C2 infrastructure
- Maintain operational security throughout an engagement
- Leverage initial access to elevate and propagate through a network
- Enumerate and attack Active Directory
- Collect and exfiltrate sensitive data in a safe manner
- New calling conventions and data types specific to Windows
- How Windows processes, threads, and services work internally
- How to abuse Windows APIs to inject shellcode into other processes without detection
- How to create a hidden, persistent service
- How to hide from user-mode tools like Task Manager
- How to create and execute shellcode without detection
- How to bypass user-land hooks and implement your own
- How to control your implant from your C2
- Create custom compiled Windows implants
- Collect target information
- Hide processes from user mode tools
- Hook and unhook functions for AV bypasses
- Generate and execute custom shellcode
- Escalate privileges from medium integrity levels to high (NT AUTHORITYSYSTEM)
- Persist across reboots
- Beacon out to configured C2 infrastructure
This course includes:
- 30+ hours of hacking content
- FREE Hacking tools, resources used in this course and latest hacking books available for Advanced Red Team Attacks.
- 24/7 availability for support, so if you have any questions you can email or chat with us and we’ll respond to you within 15 hours.
NOTES
- This course is created for educational purposes only and all the attacks are launched in my own lab or against systems that I have permission to test.
- This course is totally a product of Cyber Hacking, no other organization is associated with it or a certification exam.
Who this course is for:
- Anybody interested in learning Advanced Red Team, penetration testing and ethical hacking
- Security specialists
- Anyone interested in learning Ethical Hacking or Penetration Testing
- Anyone interested in Cyber Security
- People who want to take their Hacking skills to the next level
- People who are cyber security experts
- People who want transition to Cyber Security
- It is ideal for individuals who are currently working in the field of cyber security as well as for anyone who wishes to gain a practical understanding of how to mitigate the risks posed by malware, hackers, trackers, and other cyber threats.
- This course will tremendously benefit those who are new to the field of cyber security (cyber security students), as well as those who are looking to expand upon their existing knowledge and skills (high level professionals).


Reviews
There are no reviews yet.