This course will teach you Red Team tactics in a very practical and hands-on approach. Every lecture on a TTP (tactic, technique, and procedure) will demo commands you can follow on your own Windows lab environment..The course is divided into a number of sections, each section covers Red and Blue team skills. By the end of the course, you will have a strong foundation in Red and Blue teaming activities. How TA will compromise the environment, Real-time Attacks How Threat actors deploy Ransomware in organizations
| Course Price | Original price was: $70.00.$5.00Current price is: $5.00. |
Course Description
hat you’ll learn
- 145+ videos (30+ hours) to teach you ethical hacking & cybersecurity from scratch.
- Learn the basics of Red Team Windows tactics
- Learn basic Red Team Ethical Hacking topics
- Advanced Windows commands
- Hands-on Red Team tactics, techniques, and procedure (TTP) demos
- Learn how to abuse LOLBAS to defense evasion(Practical)
- Learn about Windows processes(Practical)
- Learn about MITRE ATT&CK framework and how to use OSINT for a real time attacks(Practical)
- Learn how to create persistence in Windows(Practical)
- Learn how to use various attack tools
- Learn how to evade defense mechanism(Practical)
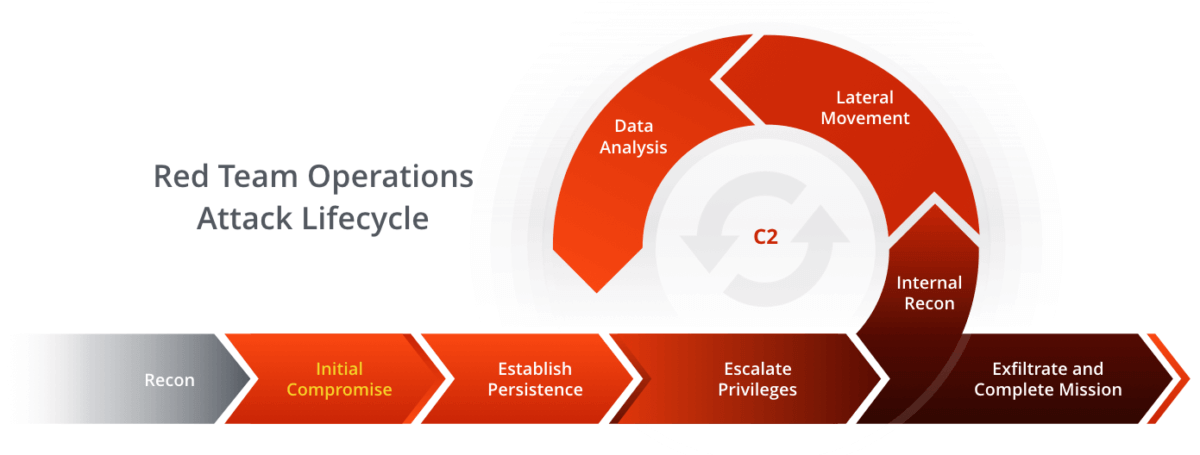
- Learn complete attack pattern Initial Access to Impact(Practical)
- Learn how to do a threat Analysis(Practical)
- Learn about the history of ransomwares
- Learn Red Teaming and Blue Teaming Activities
- Learn how threat actors will hack organization computers
- Understand attackers and their methods to defend against cyber attacks
- Concepts and terminologies of Cyber Security, Penetration Testing, Cyber Warfare, Espionage, and Crime
- Fundamental concepts of Windows Active Directory (AD)
- Key principles and techniques of cyber security for protecting against attacks
- Comprehensive coverage of the latest trends in cyber warfare, including the increasing cyber capabilities of powerful nations
- Advanced Persistent Threats ( APT ) and nation state hackers
- Simulation-based approaches to Anonymity and recent ransomware attacks
- How organizations defend themselves from sophisticated attacks
- Demonstration of a practical attack in a lab simulation
- Red Team Operations
This course includes:
- 30+ hours of hacking content
- FREE Hacking tools, resources used in this course and latest hacking books available for Red Team.
- 24/7 availability for support, so if you have any questions you can email or chat with us and we’ll respond to you within 15 hours.
NOTES
- This course is created for educational purposes only and all the attacks are launched in my own lab or against systems that I have permission to test.
- This course is totally a product of Cyber Hacking, no other organization is associated with it or a certification exam.
Who this course is for:
- Anybody interested in learning ethical hacking ,Red Team and penetration testing
- Anyone who wants to know about Red Teaming/Blue Teaming Activities
- Any who wants to enter into the emerging field of Threat Analyst/Red teamer/Cyber security Engineer
- Students who has strong desire to learn and progress in cybersecurity
- All security engineers/professionals wanting to learn advanced offensive tactics
- Red Team Operators
- Ethical Hackers
- Cybersecurity Professionals
- Penetration Testers
- Security Engineers
- System Administrators
- Network Engineers
- Security Engineers




Reviews
There are no reviews yet.