This course focuses on Advanced Evasion Techniques and Breaching Defenses, spans multiple learning modules. The initial few chapters provide a general course overview, covering Operating System, Programming Theory and Client-Side Code Execution with MS Office.
Programming Theory forms a significant part of the course, exploring areas such as executing shellcode in Word Memory, PowerShell utilization, and the intricacies of client-side code execution. The course covers creating a basic dropper in Jscript, execution with Windows Script Host, and revisiting in-memory PowerShell techniques.
| Course Price | Original price was: $100.00.$8.00Current price is: $8.00. |
Course Description
What you’ll learn
- 140+ videos (30+ hours) to teach you Advanced Evasion techniques from scratch.
- Use 50+ hacking tools
- 85+ hands-on real-life hacking examples.
- Evading Application Whitelisting
- Finding new ways to bypass AMSI
- Bypassing various Antivirus Products
- Bypassing PowerShell’s Constrained Language Mode
- Bypassing Network Filters
- Using VIM as a backdoor and keylogger
- Exploiting Linked Databases
- Unconstrained Delegation Attacks
- Resource-Based Constrained Delegation Attacks
- Taking over a domain
- Taking over a forest
- Taking over additional forests
- Bypassing Linux Antivirus Solutions
- Shared Library Hijacking
- Phishing with Microsoft Office
- Executing Shellcode in Word Memory
- Process Injection and Migration
- Introduction to Antivirus Evasion
- Advanced Antivirus Evasion
- Linux Post-Exploitation
- Windows Credentials
- Windows Lateral Movement
- Linux Lateral Movement
- Active Directory Exploitation
This course includes:
- 30+ hours of hacking content
- FREE Hacking tools, resources used in this course and latest hacking books available for Advanced Evasion techniques
- 24/7 availability for support, so if you have any questions you can email or chat with us and we’ll respond to you within 15 hours.
NOTES
- This course is created for educational purposes only and all the attacks are launched in my own lab or against systems that I have permission to test.
- This course is totally a product of Cyber Hacking, no other organization is associated with it or a certification exam.
Who this course is for:
- Anybody interested in learning Advanced Evasion techniques, penetration testing and ethical hacking
- Security specialists
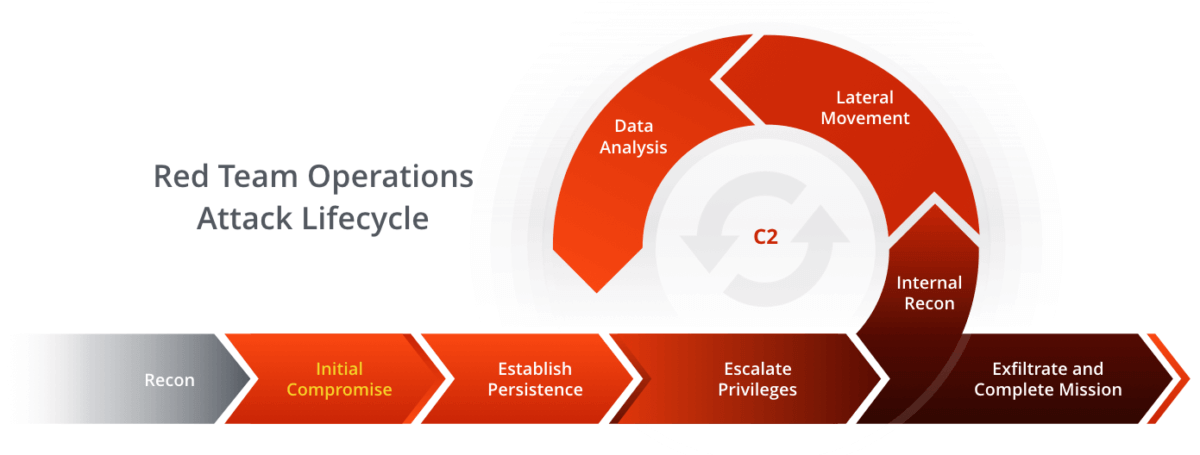
- Red Team Operators
- Ethical Hackers
- Cybersecurity Professionals
- Penetration Testers
- Security Engineers
- System Administrators
- Network Engineers
- Security Engineers



Reviews
There are no reviews yet.