Free Malware Scanner and Removal Tool
Scan and remove viruses and malware from your device with our free virus scanner and AV scanner. Our virus scan supports all devices – Windows, Mac, Android and iOS.
Get advanced virus protection and antivirus for free. Don’t worry about viruses. We scan and cleans the viruses currently on your device, and stops future viruses and threats from infecting your system. And it’s 100% free and easy to use.
Responding to an active cyberattack is difficult and chaotic. One-off remediations are no longer adequate to combat today’s relentless, persistent, and destructive threats. Many organizations don’t have the tools or bandwidth to cope.
Our Malware Removal Service gets your infected endpoints back online, minimizing disruption and ensuring continued workplace productivity. Delivered by the leaders in active threat response, Our Malware Removal Service enables your team to isolate, and remediate an attack. Our Malware Removal Specialists provide the intelligence, technology, and processes required to eradicate active threats in your environment and get your organization back on track.
Common signs of malware, viruses and cyber threats on your device
Lots of pop-ups
They might encourage you to visit unusual sites or download unfamiliar software.
Frequent crashes
Your device can freeze or crash due to hard drive damage from a virus.
Mass emails being sent in your name
Everyone’s worst nightmare: A cyberthief sends mass emails in your name.
Your password suddenly changes
Unusual stuff happens, like a password change, that keep you from logging in.
Slow computer
If your computer suddenly starts running slowly, it could be a virus.
Your homepage is different
Your homepage defaults to a different website or you can’t reset it
Ransomware symptoms
Your device is locked
A splash screen appears upon startup that asks for payment and you can’t login.
Odd or missing file extensions
Files have extensions like .crypted or .cryptor or their extensions are missing altogether.
Files won’t open
You get an unusual error message that Windows or iOS are unable to open or find specific files.
You receive a payment notice
The hacker that infected your device gave you instructions on how to make payment.
Suspicious Emails
Phishing is one of the most common ways that a ransomware attack begins.
Unexpected Network Scanners
Cybercriminals wi’ll do some digging into your network and find out the domain rights of that computer, and what else they can gain access to.
Remove Virus from Android Phones and iPhones
How to get rid of a virus from an Android phone
Clear your cache and downloads.
Open Settings, go to Apps & notifications, and select Chrome. In the Storage & cache menu, follow the steps to clear your cache and storage.
Restart your Android device in safe mode.
Press and hold the power button, then choose the option to restart your phone in safe mode. You’ll see Safe Mode in the corner of your screen after your phone reboots.
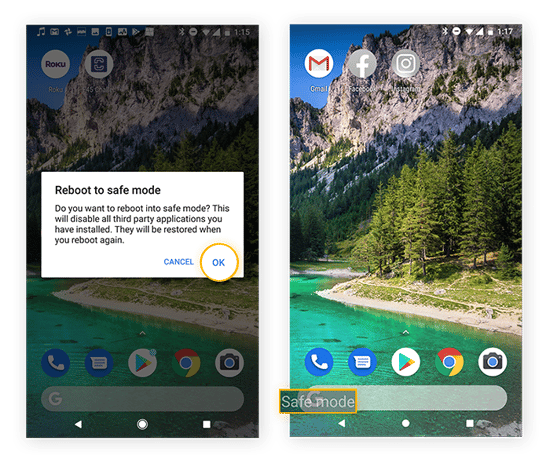
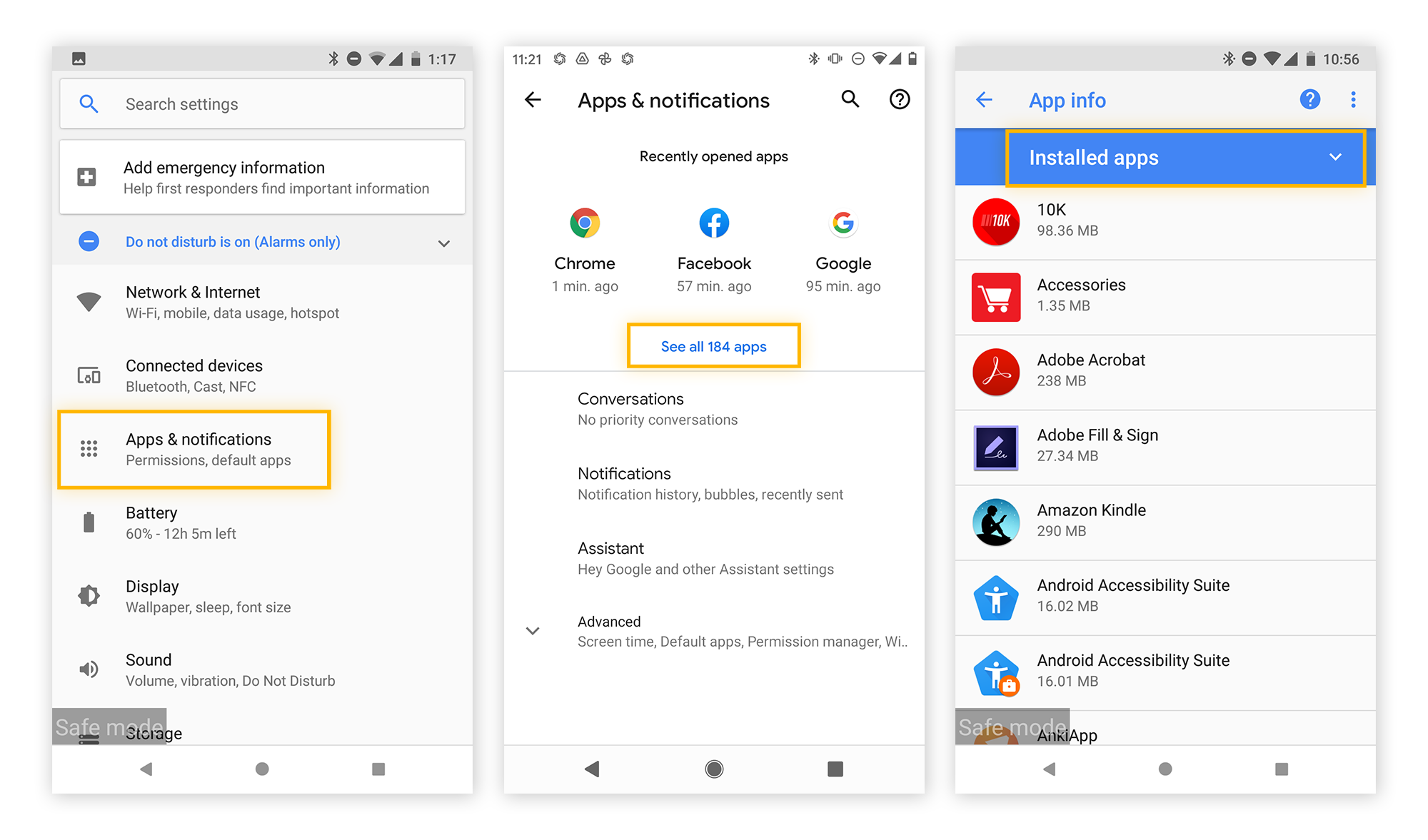
Find and remove malicious apps.
Open Settings and tap Apps & notifications. Then tap See all apps. On the next screen, select Installed apps in the drop-down menu. Review your installed apps — if you see any that are suspicious or unfamiliar, uninstall them. Then restart your phone.
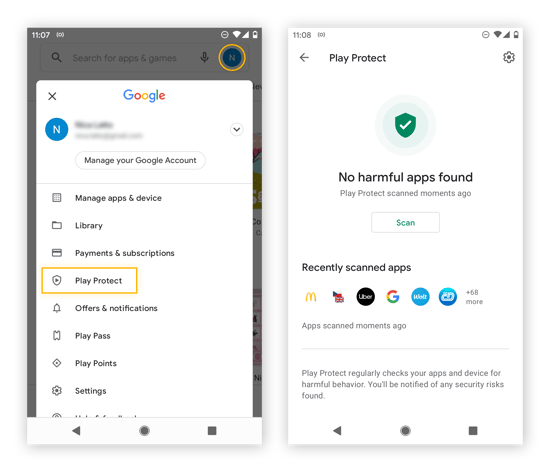
Activate Google Play Protect.
The Play Protect feature in the Google Play Store monitors apps for unusual behavior that can indicate the presence of Android malware. Open the Play Store app, tap your icon or avatar in the top right, and activate Play Protect in the menu.
Contact US
How to remove a virus from an iPhone
A lot of iPhone malware is caused by hackers manipulating your browser. That’s why clearing your browsing history and data can help resolve iPhone virus issues. But to remove iPhone spyware and more insidious malware threats, you’ll likely need to restart your iPhone, update iOS, restore your phone to a previous backup, or perform a factory reset.
If you think your iPhone has a virus, here are a few ways to get rid of the malware infection:
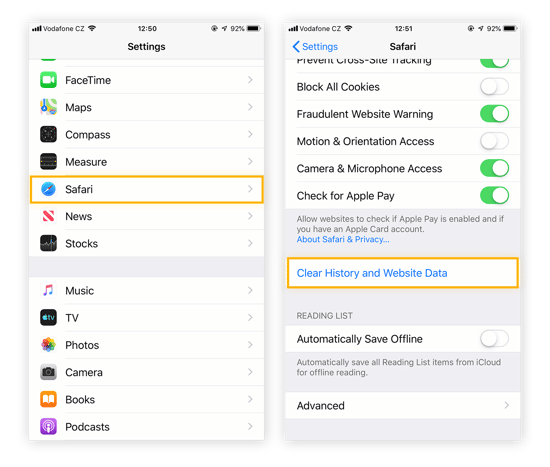
Clear your browsing history and data.
Open Settings, scroll and tap Safari, and then tap Clear History and Website Data.
Repeat this process for any other browsers you use.
Restart your phone.
Hold the power button and turn off your phone. Wait a few seconds and turn it back on.
Update iOS.
Go to Settings > General > Software Update. If you see a software update, install it.
Restore your iPhone to a previous backup.
Go to Settings > General > Reset, then choose Erase All Content and Settings. Follow the prompts to restore your iPhone from a backup. Choose a backup you created from before your phone began acting strangely.
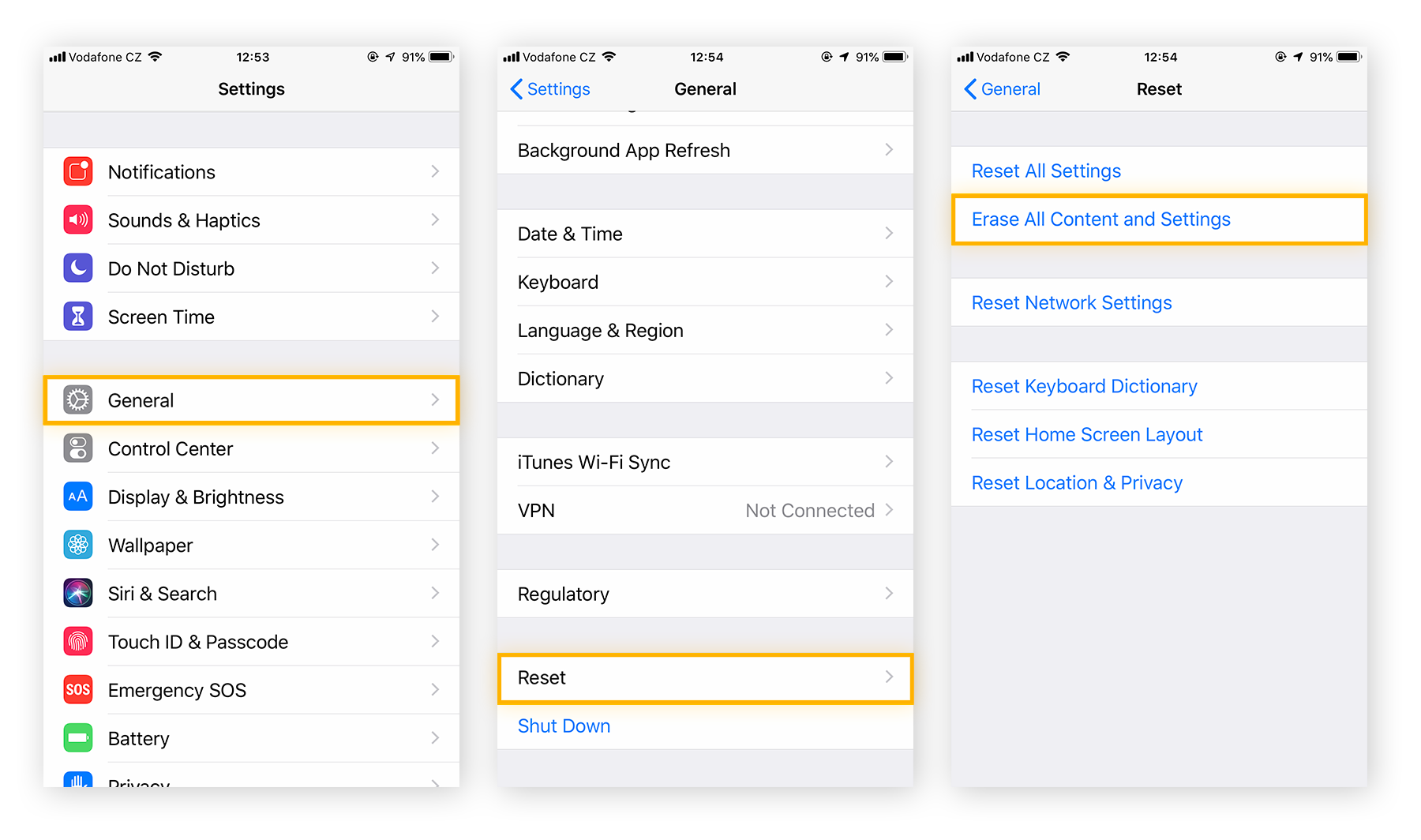
Reset your iPhone to its factory settings.
If your iPhone is still acting up, go to Settings > General > Reset, and choose Erase All Content and Settings. Here, rather than restore from a previous iCloud backup, choose the option to reset your phone.
Contact US.
All about ransomware attacks
Ransomware made headlines throughout 2021 and continues to make the news in 2022. You may have heard stories of attacks on large companies, organizations, or government agencies, or perhaps you as an individual have experienced a ransomware attack on your own device.
It’s a significant problem and a scary prospect to have all of your files and data held hostage until you pay up. If you want to know more about this threat, read on to learn about ransomware’s different forms, how you get it, where it comes from, who it targets, and ultimately, what you can do to protect against it.
Ransom malware, or ransomware, is a type of malware that prevents users from accessing their system or personal files and demands ransom payment in order to regain access. While some people might think “a virus locked my computer,” ransomware would typically be classified as a different form of malware than a virus.
The earliest variants of ransomware were developed in the late 1980s, and payment was to be sent via snail mail. Today, ransomware authors order that payment be sent via cryptocurrency or credit card, and attackers target individuals, businesses, and organizations of all kinds. Some ransomware authors sell the service to other cybercriminals, which is known as Ransomware-as-a-Service or RaaS.
How do I get ransomware?
- Malspam: To gain access, some threat actors use spam, where they send an email with a malicious attachment to as many people as possible, seeing who opens the attachment and “takes the bait,” so to speak. Malicious spam, or malspam, is unsolicited email that is used to deliver malware. The email might include booby-trapped attachments, such as PDFs or Word documents. It might also contain links to malicious websites.
- Malvertising: Another popular infection method is malvertising. Malvertising, or malicious advertising, is the use of online advertising to distribute malware with little to no user interaction required. While browsing the web, even legitimate sites, users can be directed to criminal servers without ever clicking on an ad. These servers catalog details about victim computers and their locations, and then select the malware best suited to deliver. Often, that malware is ransomware. Malvertising often uses an infected iframe, or invisible webpage element, to do its work. The iframe redirects to an exploit landing page, and malicious code attacks the system from the landing page via exploit kit. All this happens without the user’s knowledge, which is why it’s often referred to as a drive-by-download.
- Spear phishing: A more targeted means to a ransomware attack is through spear phishing. An example of spear phishing would be sending emails to employees of a certain company, claiming that the CEO is asking you to take an important employee survey, or the HR department is requiring you to download and read a new policy. The term “whaling” is used to describe such methods targeted toward high-level decision makers in an organization, such as the CEO or other executives.
- Social engineering: Malspam, malvertising, and spear phishing can, and often do, contain elements of social engineering. Threat actors may use social engineering in order to trick people into opening attachments or clicking on links by appearing as legitimate—whether that’s by seeming to be from a trusted institution or a friend. Cybercriminals use social engineering in other types of ransomware attacks, such as posing as the FBI in order to scare users into paying them a sum of money to unlock their files. Another example of social engineering would be if a threat actor gathers information from your public social media profiles about your interests, places you visit often, your job, etc., and using some of that information to send you a message that looks familiar to you, hoping you’ll click before you realize it’s not legitimate.
CONTACT US
Ethical Hacking Courses
- All
- Cloud Hacking
- Ethical Hacking
- Internet Frauds
- Malware
- OSINT
- Penetration Testing
- Red Team
- Social Engineering