What is Hacking?
Hacking is the process by which a person or group of people gains unauthorized access to data in a network, system, or computer. It’s also a major area of concern in cybersecurity. There are different types of hackers, often referred to as various colored “hats” within the industry. These include black hat, white hat, red hat, gray hat, green hat, and blue hat hackers.
Black hat hackers take advantage of vulnerabilities in computer systems to disable an individual’s or organization’s operations. They create malicious software (“malware”) programs that help them gain access to computer networks. Once they have access to a system, black hat hackers can spy on victims’ online activities and steal sensitive information to ransom for a price.
White hat hackers also infiltrate computer systems, but they do so without malicious intent. Instead, their goal is to help organizations uncover and fix system vulnerabilities that could be exploited by black hat hackers if left unchecked. By thinking like cybercriminals and anticipating malicious actions, ethical hackers can strengthen a company’s security infrastructure.Footnote 3
Hacking can cause serious financial and reputational damage. As a result, modern businesses must rely on strong defensive and offensive security measures to ensure sensitive information isn’t accessed, manipulated, or stolen. Ethical hackers provide an added layer of security for companies that are prioritizing the safety of their assets and workforce from cybercriminals.
Cybersecurity professionals work on the digital front lines to protect organizations from malicious actors every day. If computer systems and cybersecurity excite you, ethical hacking could be a great career fit for you.
Featured Hacking Courses
Web Application Hacking
The course covers popular website hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Mobile Hacking
The course covers popular mobile hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Computer Hacking
The course covers popular computer hacking technique and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Web Server Hacking
The course covers popular database hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Wifi Hacking
The course covers popular WiFi hacking techniques and the course dives much deeper in this topic covering more techniques, How to tell if your wifi is hacked and how to fix it.

Network Hacking
The course covers popular network hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Databse Hacking
The course covers popular database hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.
Social Engineering (Basics)
The course covers popular social engineering hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Bluetooth & Radio Hacking
The course covers popular bluetooth and radio hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

IOT Hacking
The course covers popular iot hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Active Directory Hacking
The course covers popular active directory hacking techniques and the course dives much deeper in this topic covering more techniques, advanced post exploitation, bypassing security and more.

Hacking With Burp Suite
The course covers how to use burp suite. Burp is one of the top-rated security suites for pentesting and ethical hacking.The Burp suite is widely used by security professionals to perform advanced scans

Hacking With Metasploit
The Metasploit course will break it down for you step-by-step. From understanding what exactly Metasploit is to setting it up and exploring its various modules, we'll guide you through every aspect of how to use Metasploit effectively.

Bug Bounty Hunter (Basics)
Best in-depth course on practical bug bounty hunting with ethical hacking. Bug bounty programs reward anyone who reports an exploit or security vulnerability, sometimes even paying up to hundreds of thousands of dollars.

Hacking With Kali Linux
In this coure, we’ll focus primarily on how to use this powerful OS to run a pentest and mistakes to avoid. This course serves as an introduction to common pentesting phases, with practical examples that highlight best practices

Ethical Hacking Course (Basics)
This course will introduce learners to computer and network security concepts such as threats and vulnerabilities, password cracking, web application attacks, IoT and OT attacks, cloud computing, pentesting fundamentals, and more.

Penetration Testing Course (Basics)
If you’re interested in penetration testing training, online courses can offer hands-on experience applying the cybersecurity technique. In order to supplement your penetration testing knowledge and round out your cybersecurity skill set.

Red Team Course (Basics)
This course includes performing adversary emulation, a type of Red Team exercise where the Red Team emulates how an adversary operates, following the same tactics, techniques, and procedures (TTPs), with a specific objective similar to those of realistic threats or adversaries.

OpenSource Intelligence - OSINT (Basics)
This course is comprehensive training course on Open-Source Intelligence (OSINT). The course is designed to teach you the most important skills, tools, and methods needed to launch or further refine your investigation skills.

Ethical Hacking Course (Advanced)
Students with the prerequisite knowledge to take this course will walk through dozens of real-world attacks used by the most seasoned ethical hackers. The methodology of a given attack is discussed, followed by exercises in a hands-on lab to consolidate advanced concepts.

Bug Bounty Hunter (Advanced)
A bug bounty advanced course equips you with the knowledge and techniques to become a advanced bug bounty hunter. This course is intended for students or general infosec enthusiast who wish to know more about the side of bug bounties.

OpenSource Intelligence - OSINT (Advanced)
This is an advanced Open-Source Intelligence (OSINT) course for those who already know the foundations of OSINT. The goal is to provide students with more in-depth and technical OSINT knowledge.

Penetration Testing Course (Advanced)
This course is for those with existing penetration testing experience. The methodology of a given attack is discussed, followed by exercises in a hands-on lab to consolidate advanced concepts and facilitate the immediate application of techniques in the workplace
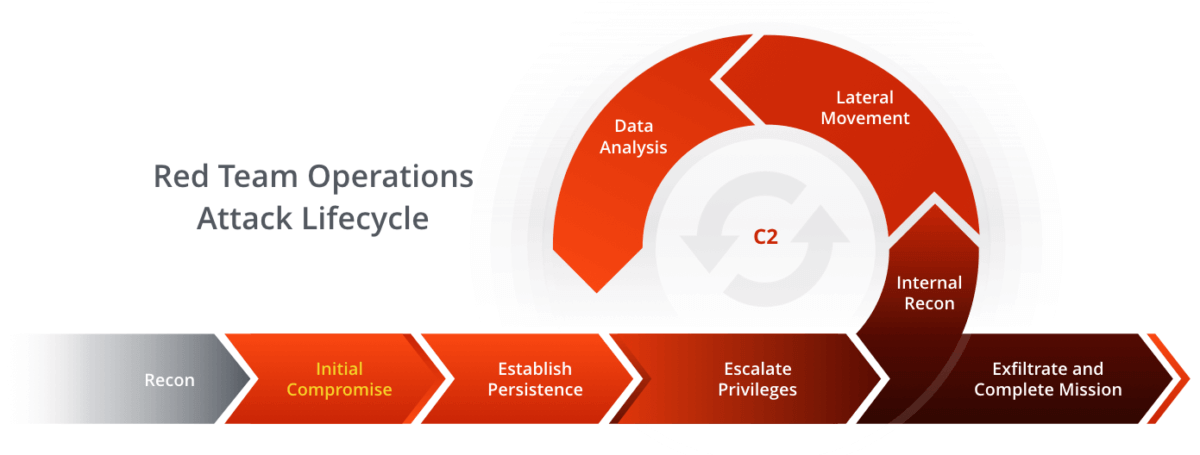
Red Teaming Course (Advanced)
Our red team advanced course training is designed to give you the skills and insights to thrive in the world of cybersecurity. With experienced instructors leading the way, you dive deep into the fundamentals of cybercrime assaults and gain firsthand experience.

Password Cracking (Basics)
Learn new password cracking techniques, how to tailor these to the hashes you have, and more during this intensive training with In.security. We specialize in password cracking and have given several conference talks on the topic. Password crackers are essential tools in any pen tester's toolbox.
Evading Security Controls (Basics)
Learn how hackers bypass security controls and hack or compromise a network, system or online devices.We will briefly cover how hackers exploit them to circumvent security controls, and what defenders can do to mitigate this threat.

Pivoting & Lateral Movement (Basics)
In this course you will learn how Lateral movement enables attackers to explore the network, escalate privileges and access sensitive data. The goal is to remain undetected and establish a more substantial and persistence presence within the compromised network.

Cloud Hacking (Basics)
The course dives into topics of classic cloud Virtual Machines, buckets, and other new issues that appear in cloud-like microservices, in-memory data stores, files in the cloud, serverless functions, Kubernetes meshes, and containers. It also covers Azure and AWS penetration testing.

Cloud Hacking (Advanced)
This course cuts through the mystery of Cloud Services (including AWS, Azure, and Google Cloud Platform) to uncover the vulnerabilities that lie beneath. We will cover a number of popular services and delve into both what makes them different, and what makes them the same, as compared to hacking and securing traditional network infrastructure.
Building Hacking Lab Environment
We’ll cover a basic setup that has your attack box and a vulnerable machine to work on. We’ll chain vulnerable machines together, so you have a virtual lab network to practice pivoting through. We’ll get you going on an Active Directory domain controller. Will, help you build your own vulnerable, multi-machine..

Password Cracking (Advanced)
In this course, you will get a hands-on experience of a huge variety of modern password cracking techniques with this course. Traditional password attacks failing you? Increase your success rate with hybrid, combinator/passphrase, PRINCE and fingerprint attacks from our team. We’ll even sure you how to attack foreign language passwords and emojis!

Evading Security Controls (Advanced)
In this course, you'll learn how to go undetected and penetrate deeper into systems and networks for maximum effectiveness. Next, you'll discover how to bypass network and application firewalls. Then, you'll learn how to sneak past intrusion detection systems and honeypots. Finally, you'll learn circumventing application security controls and how to fool anti-virus software

Pivoting & Lateral Movement (Advanced)
In this course,you will learn how to utilize CME for Windows AD navigation in a Red Team environment.Next, you'll discover how to gather credentials from endpoints and possibly domain controllers and use them to further the penetration of the AD network. Finally, you'll learn that you won’t always need to crack the password to authenticate against systems.

Prevent Getting Hacked Online
These days it seems like everybody is getting hacked. There are hundreds of successful cyber-attacks a year and countless attempts. While you can’t fully protect yourself from hacking, you can help prevent it from happening. This course will teach you how to increase the security of your accounts, mobile devices, computers, and networks.

Remove Malware From Infected Devices
A device already compromised by malware could get on your network, people can personally place malware on a system, and some malware sits there, dormant, waiting to come to life and attack. In this course we will teach you how to remove malware, ransomware or virus from you device.

Social Engineering (Advanced)
The course provides tools and techniques for testers to identify flaws in their environments that are vulnerable to social engineering attacks. Defenders taking this course will note common tools and techniques that will enable them to prepare responses and countermeasures within their organizations.